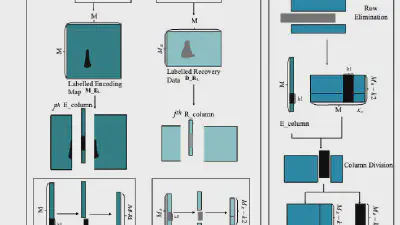
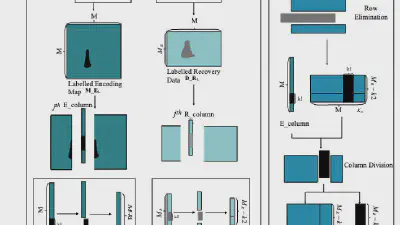
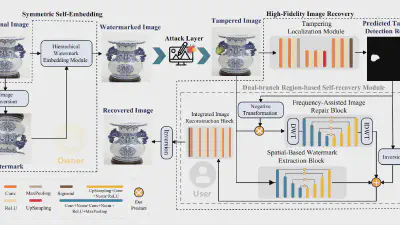
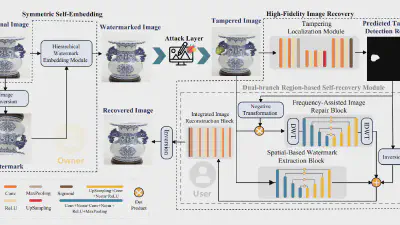
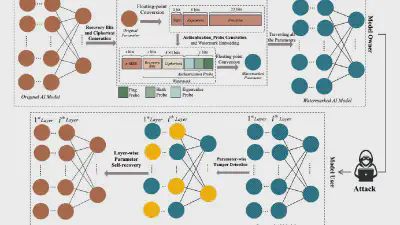
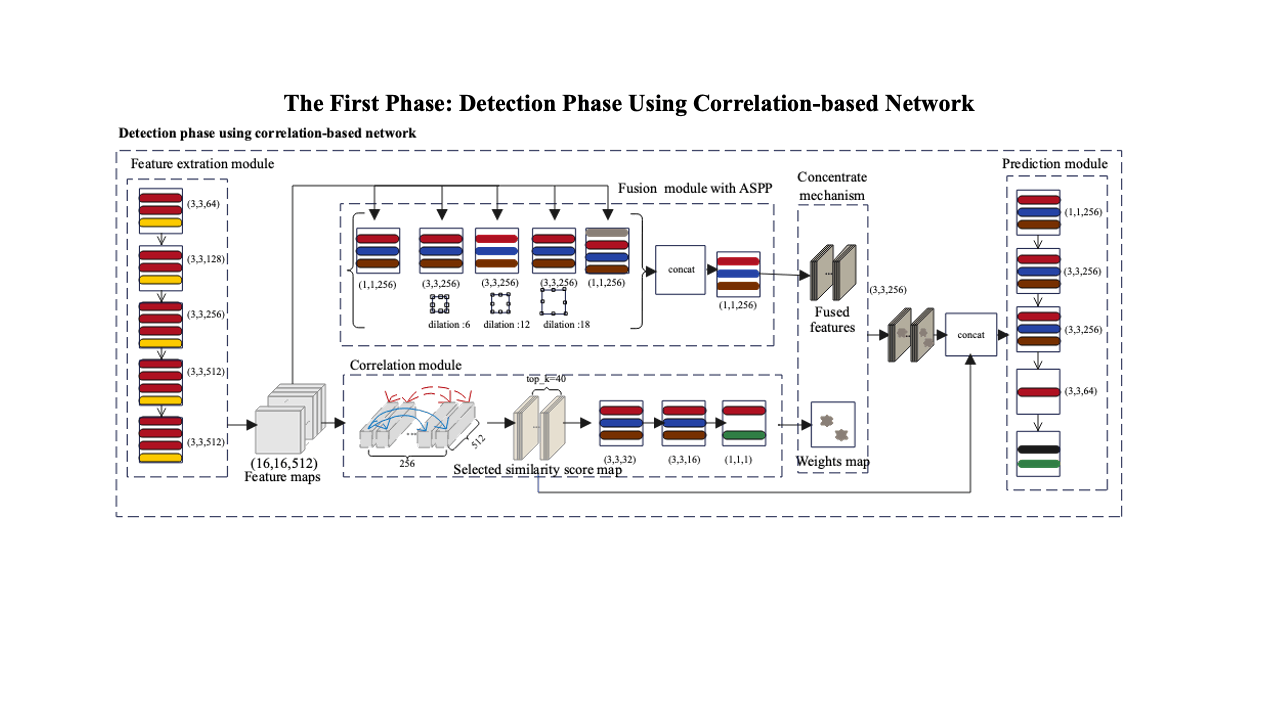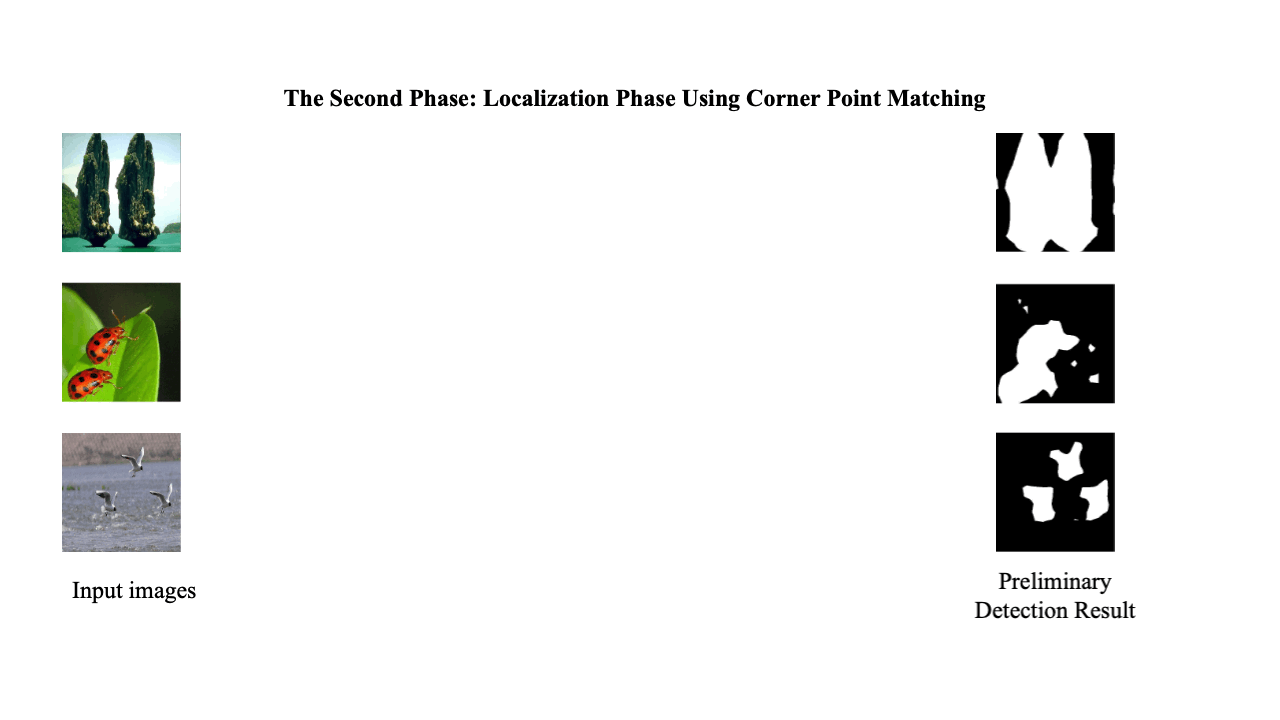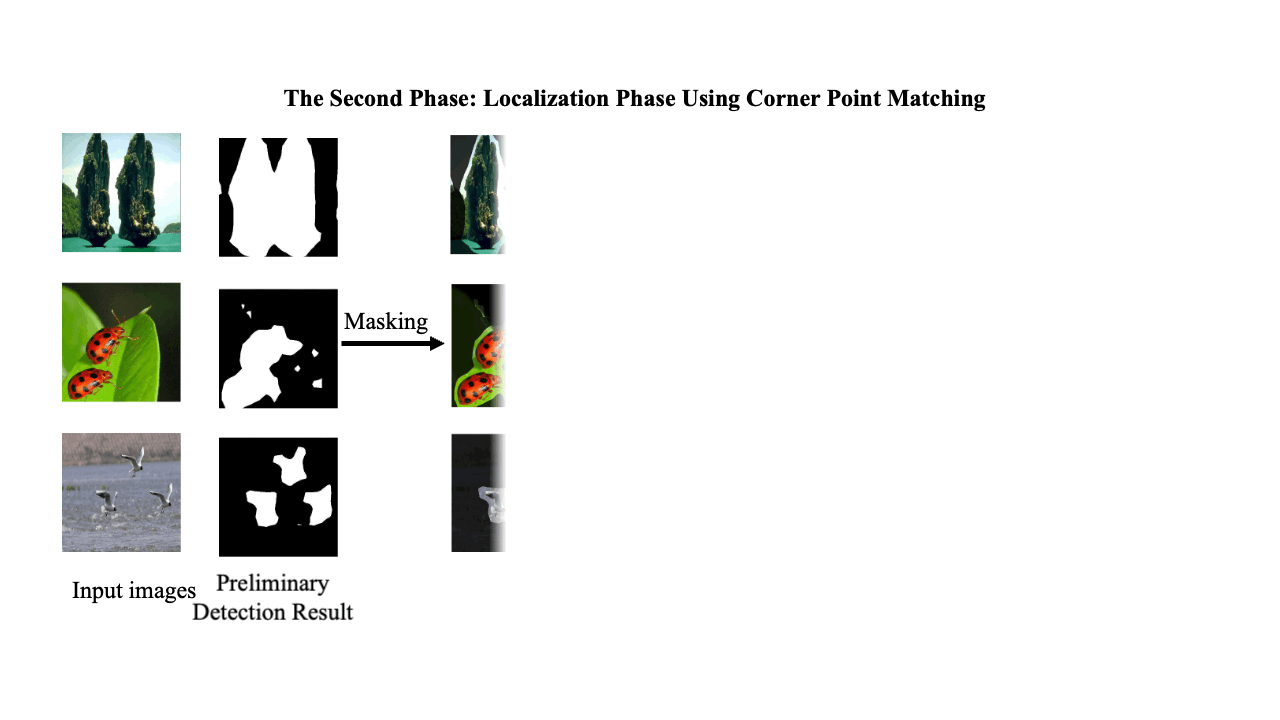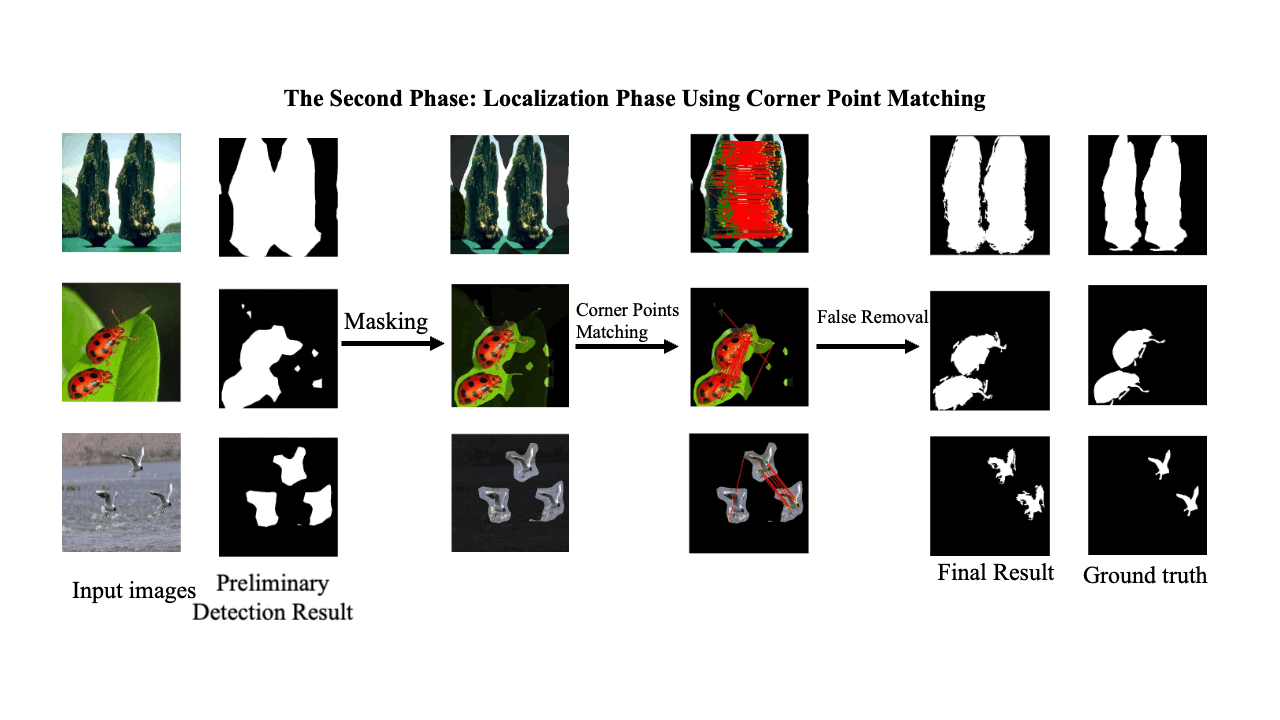
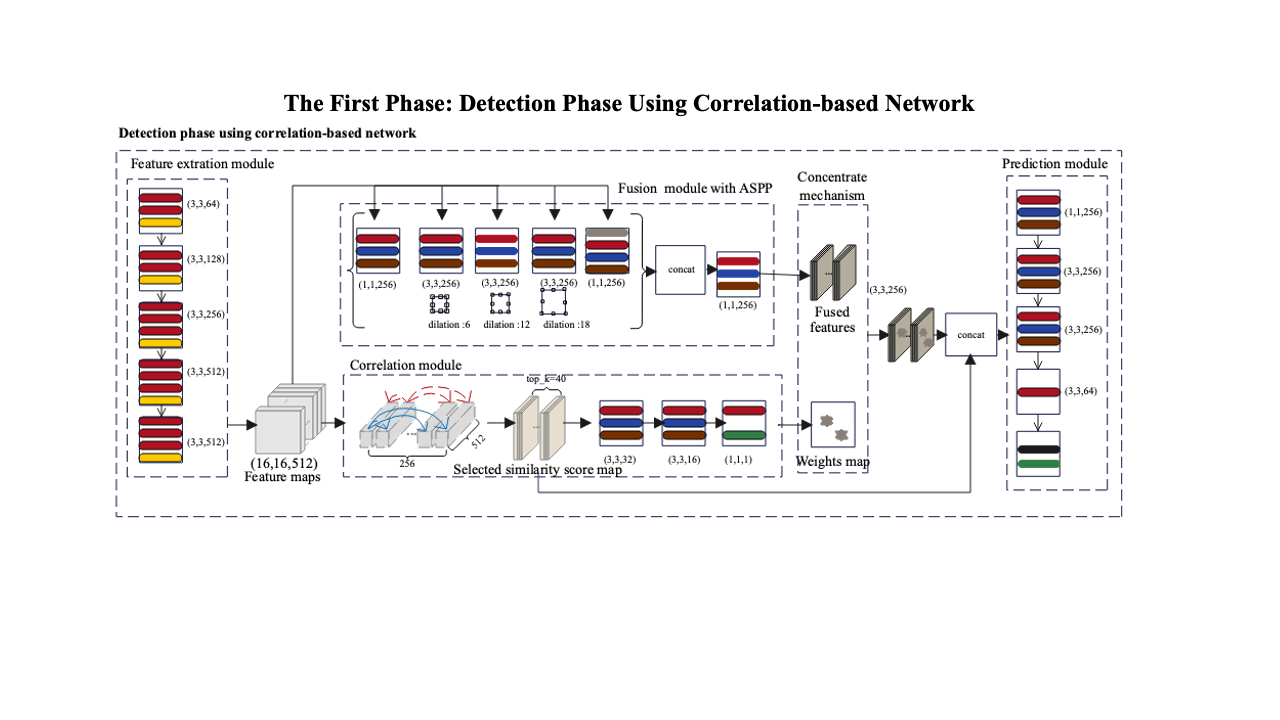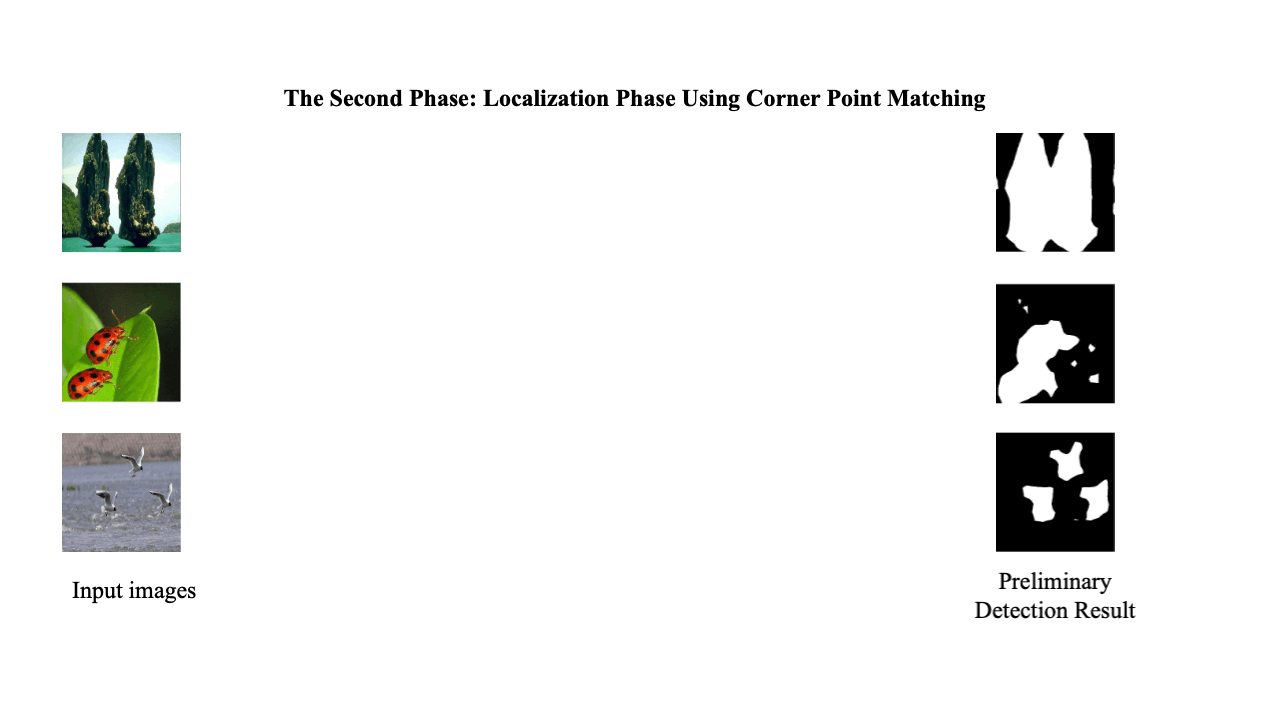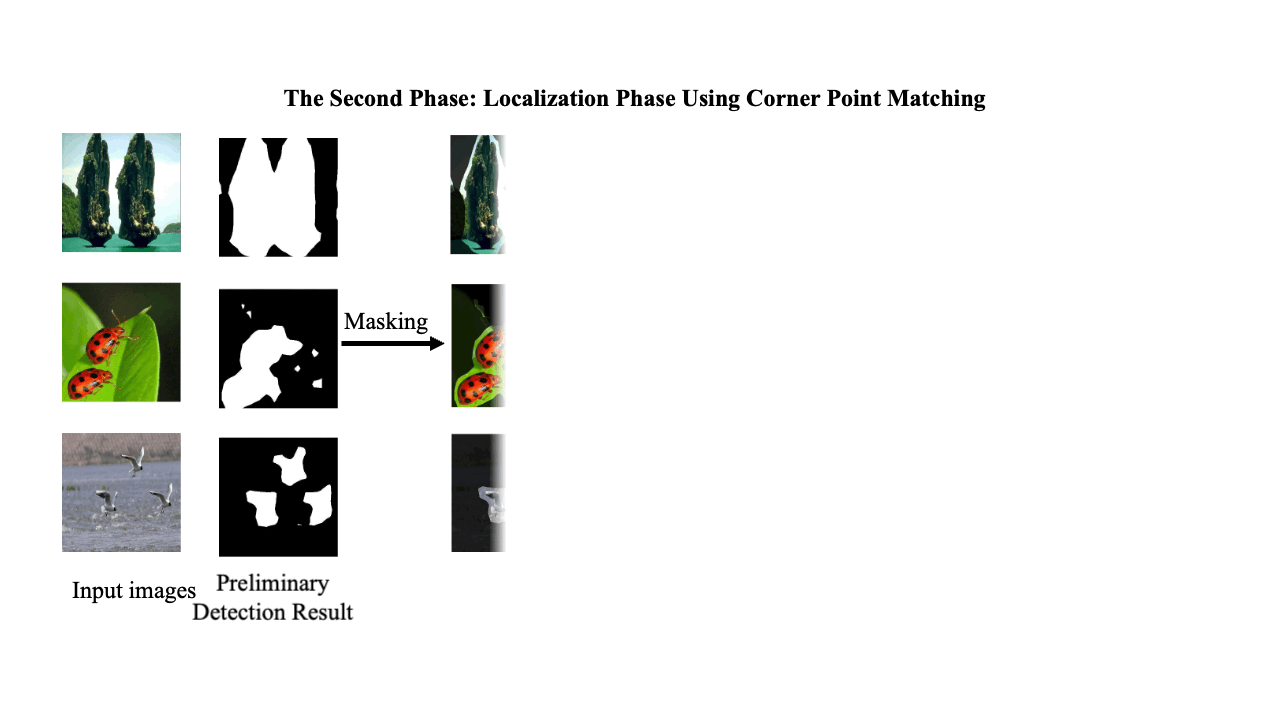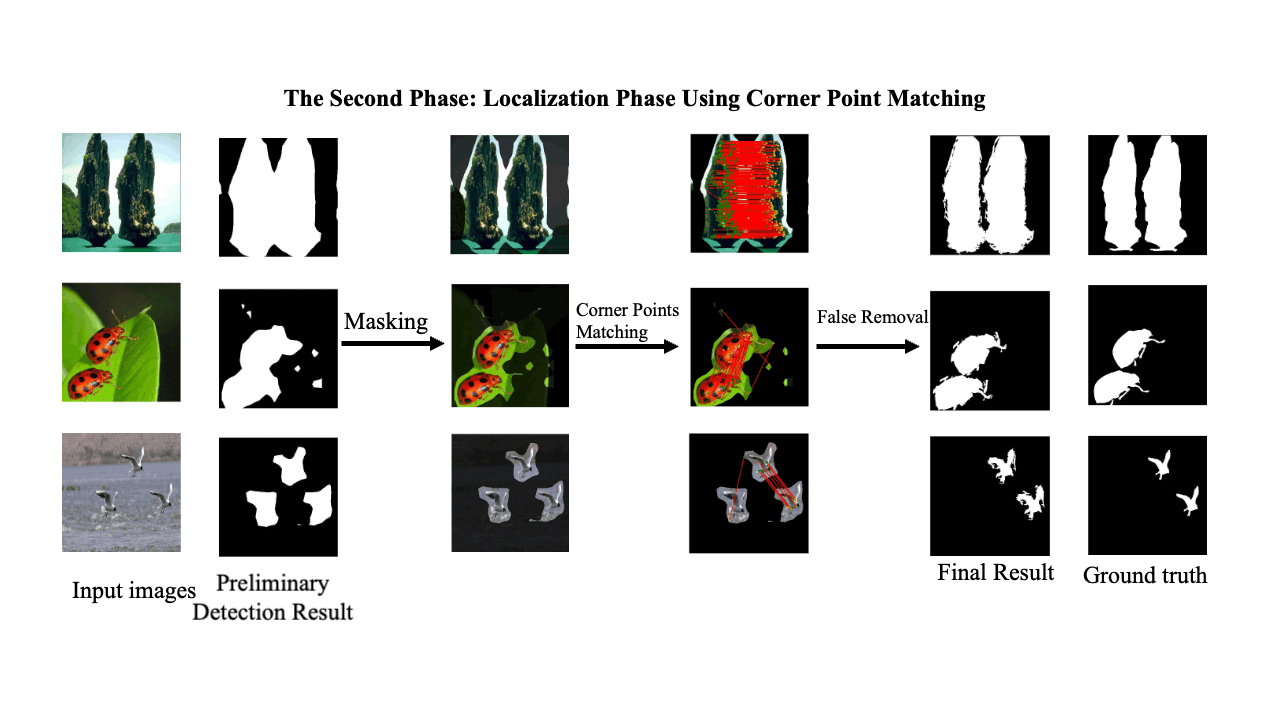
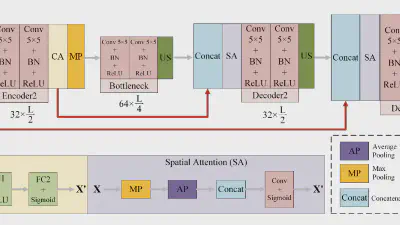
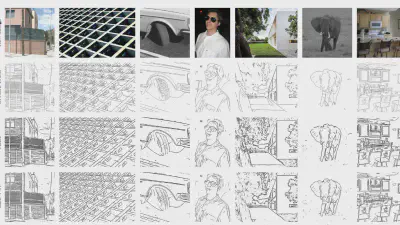
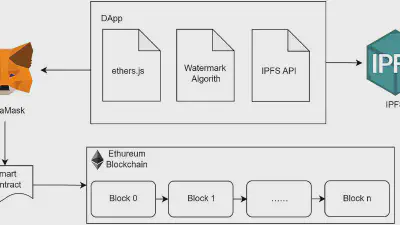
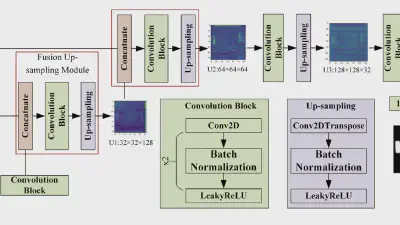
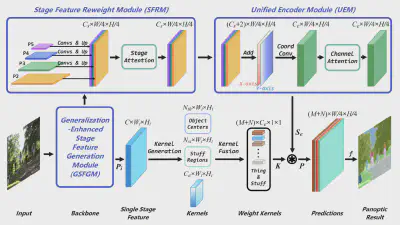
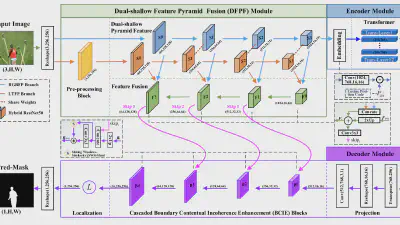
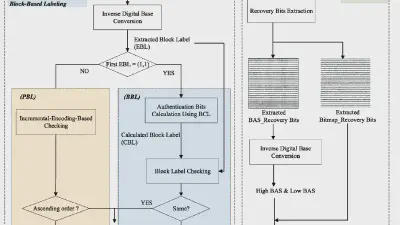
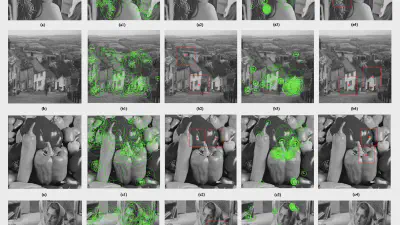
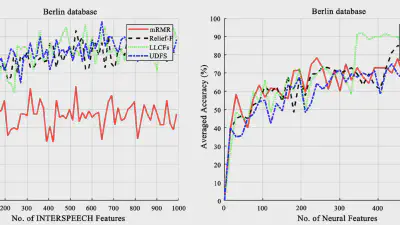
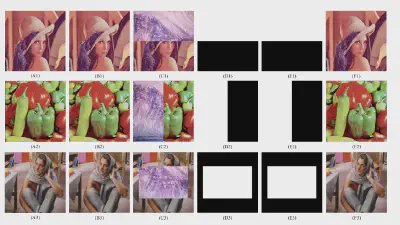
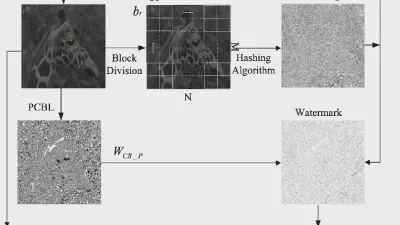
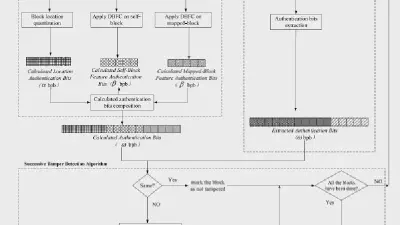
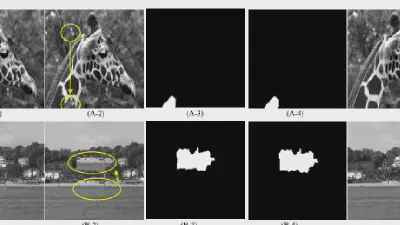
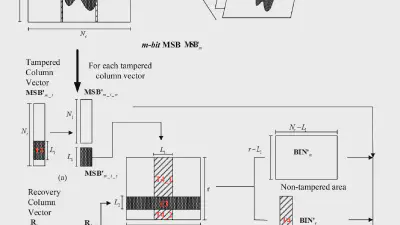
Decoding coefficients recovery based on modified gauss-jordan elimination for tampered content reconstruction
The widespread availability of image editing applications has increased the risk of digital image tampering. Although existing studies can accurately localize tampered regions, …