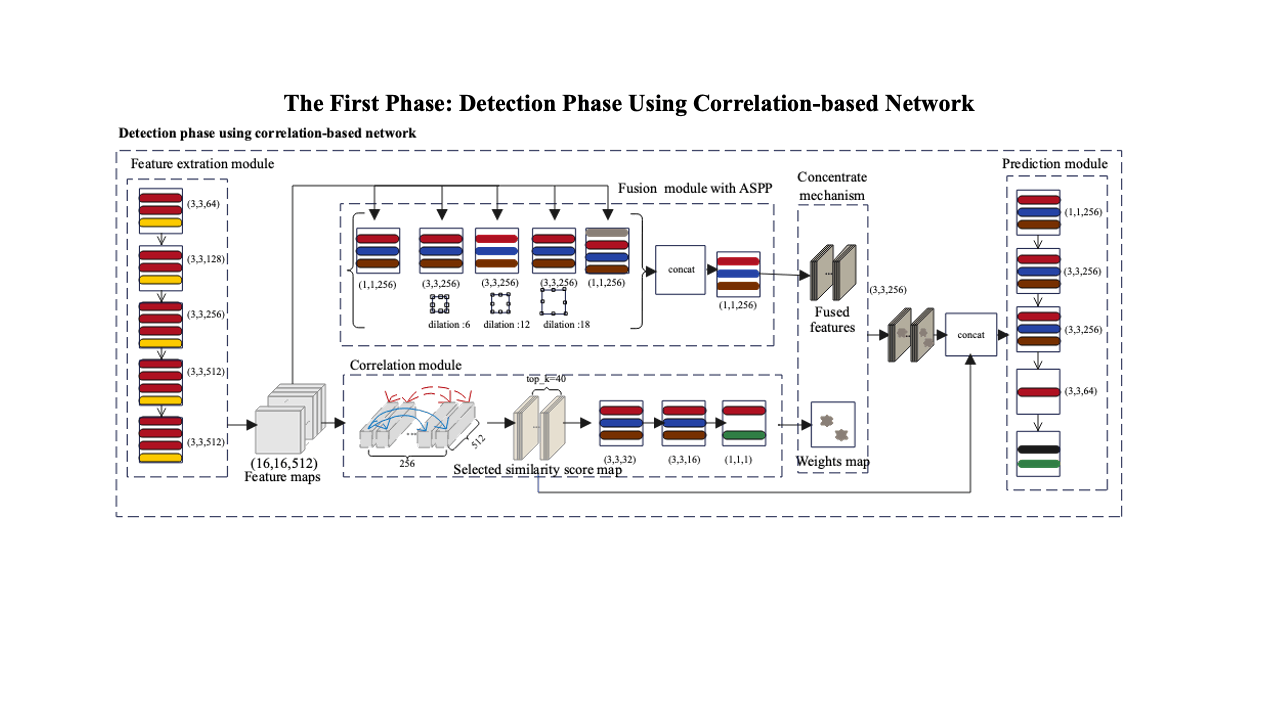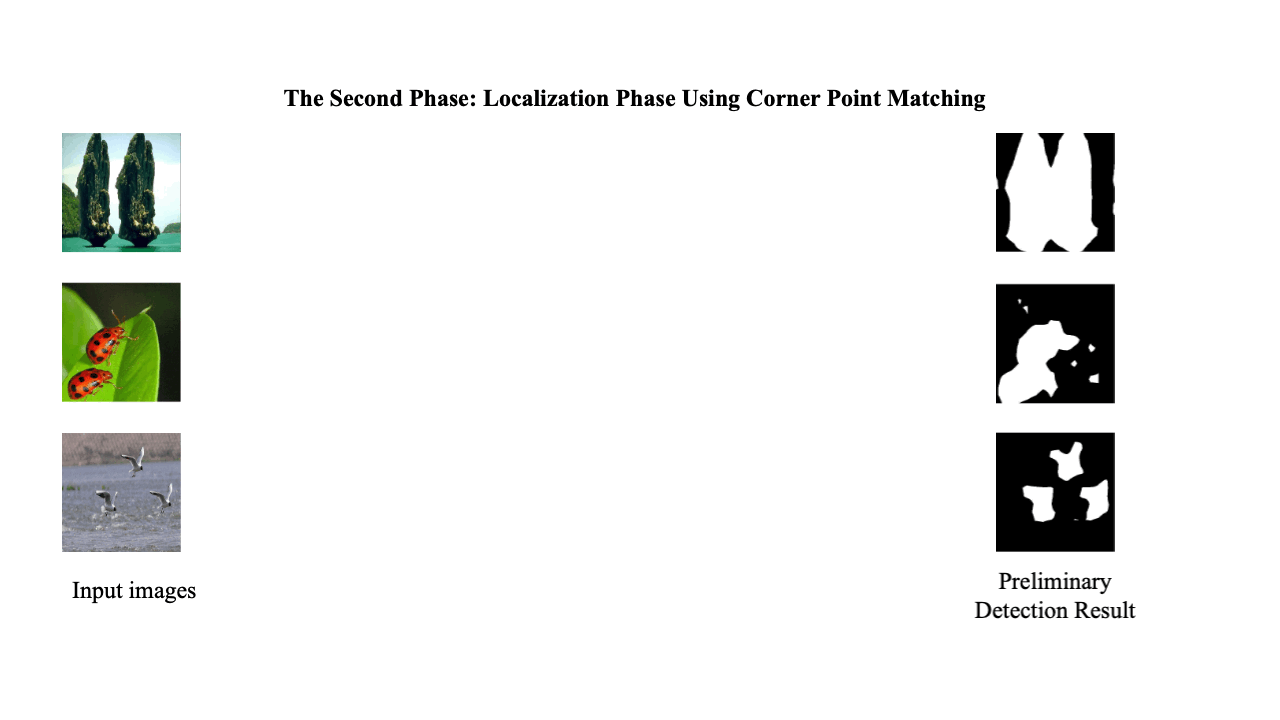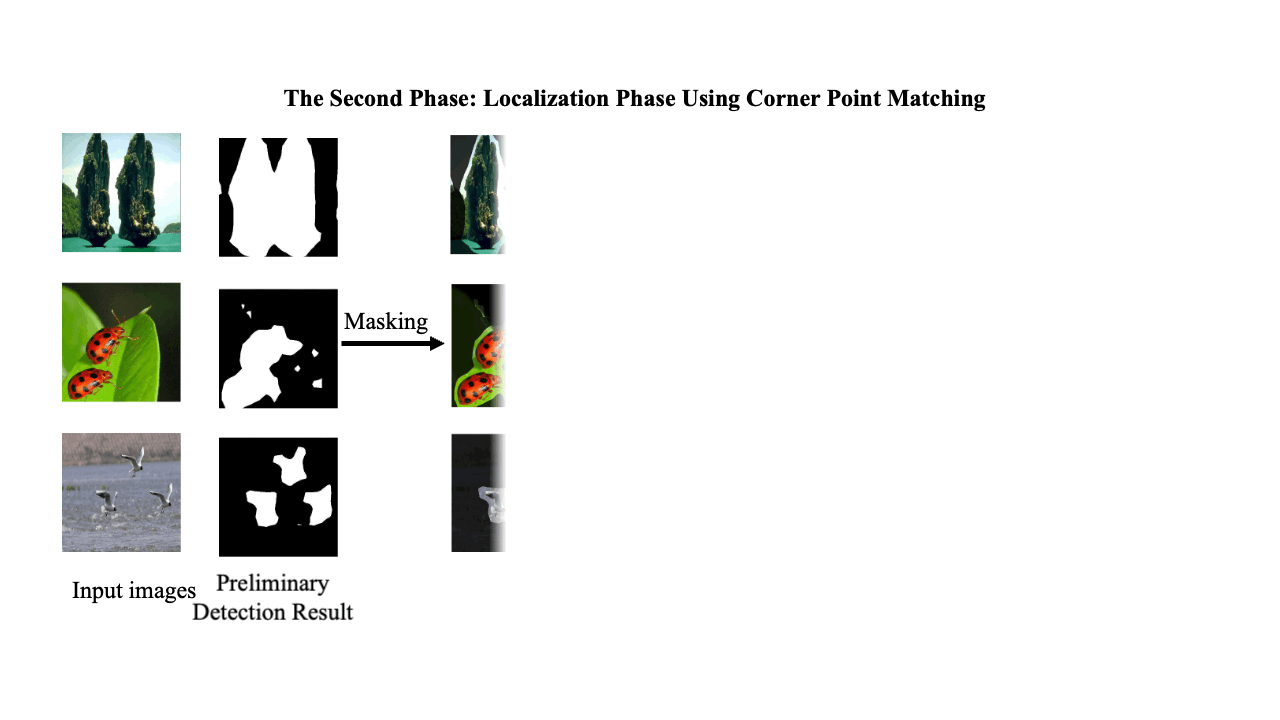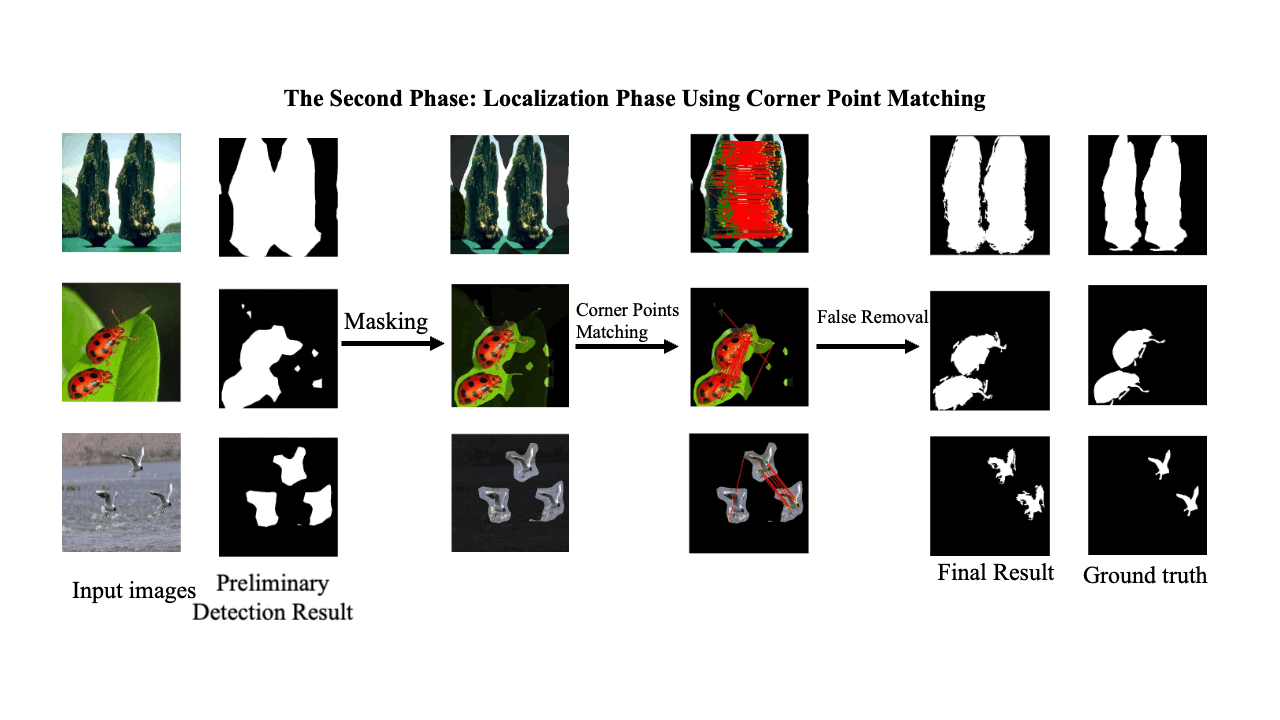
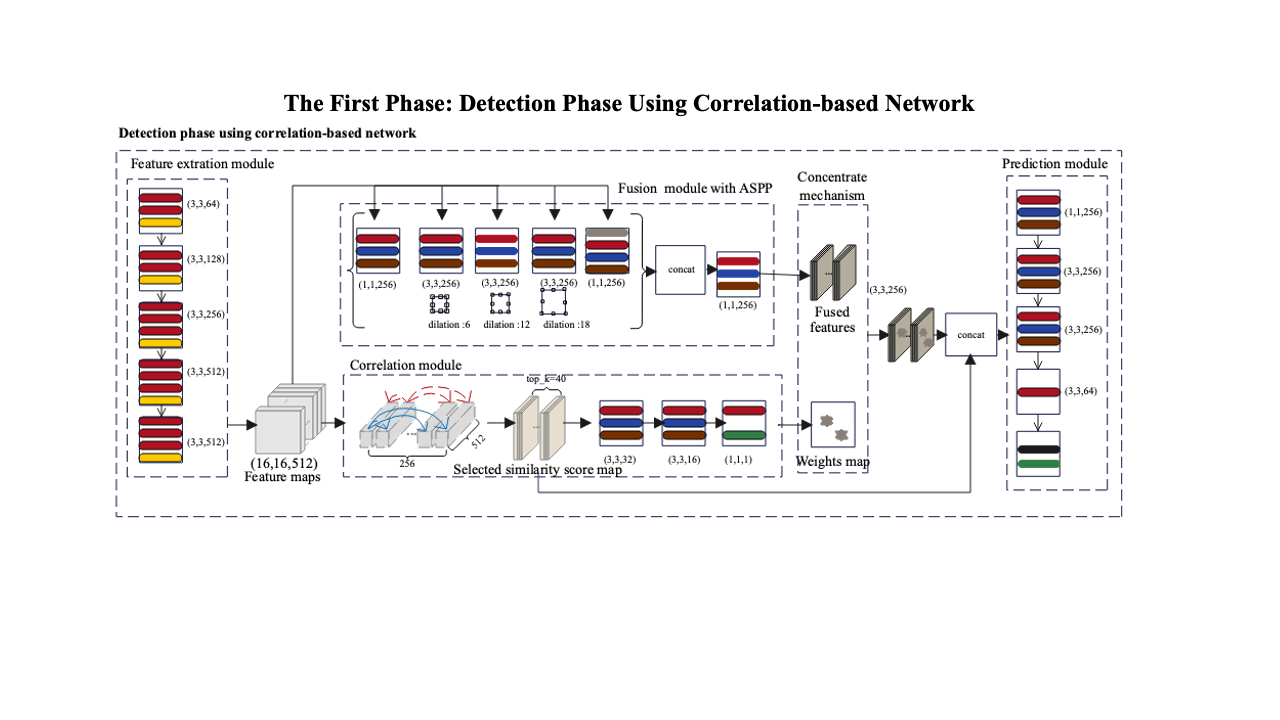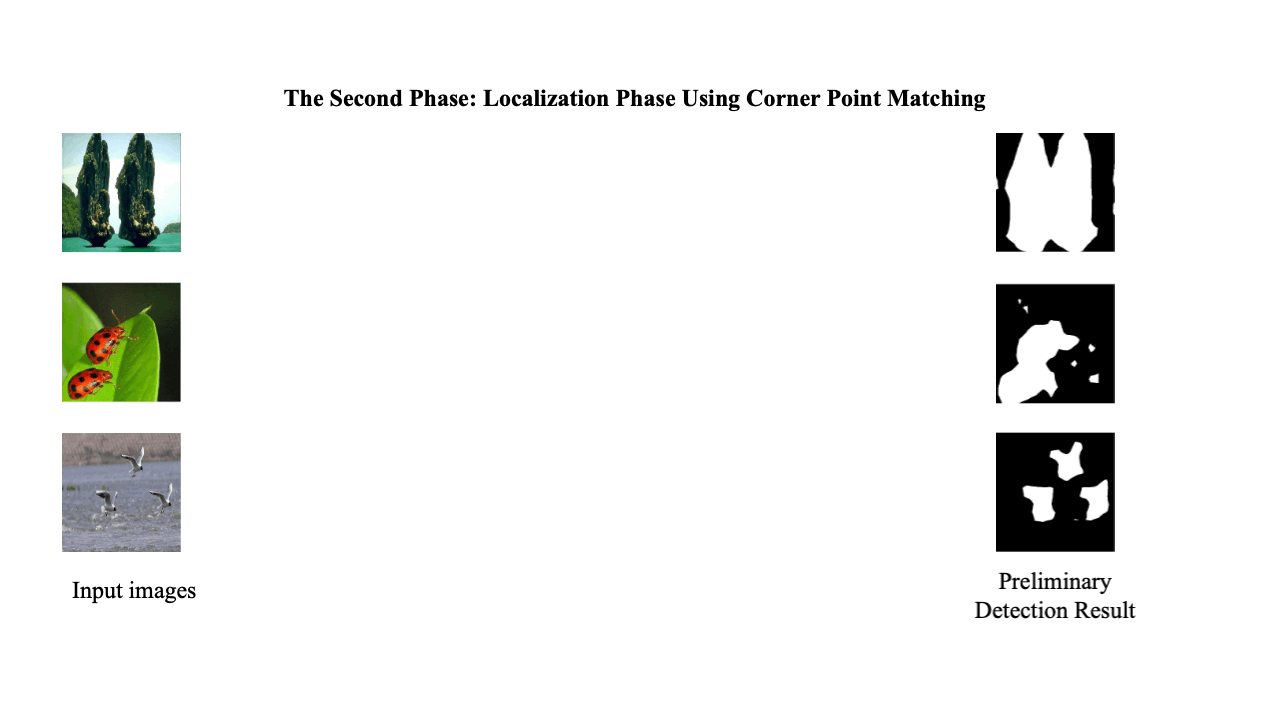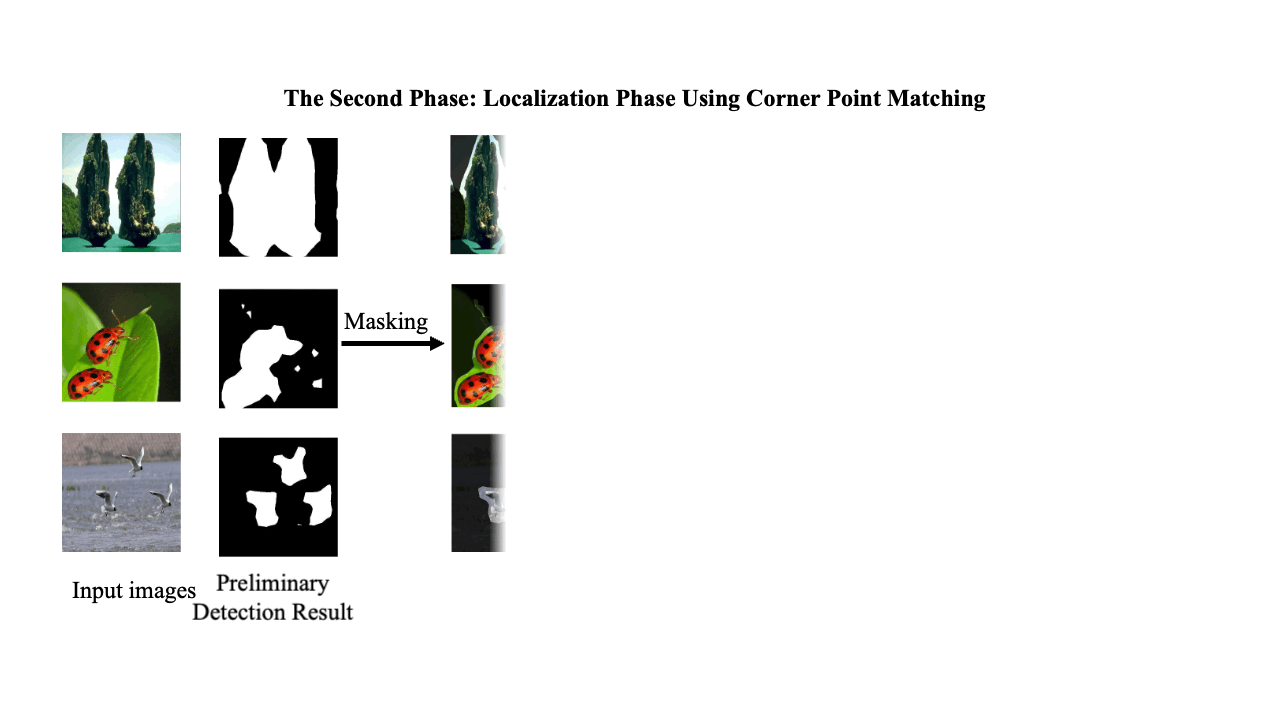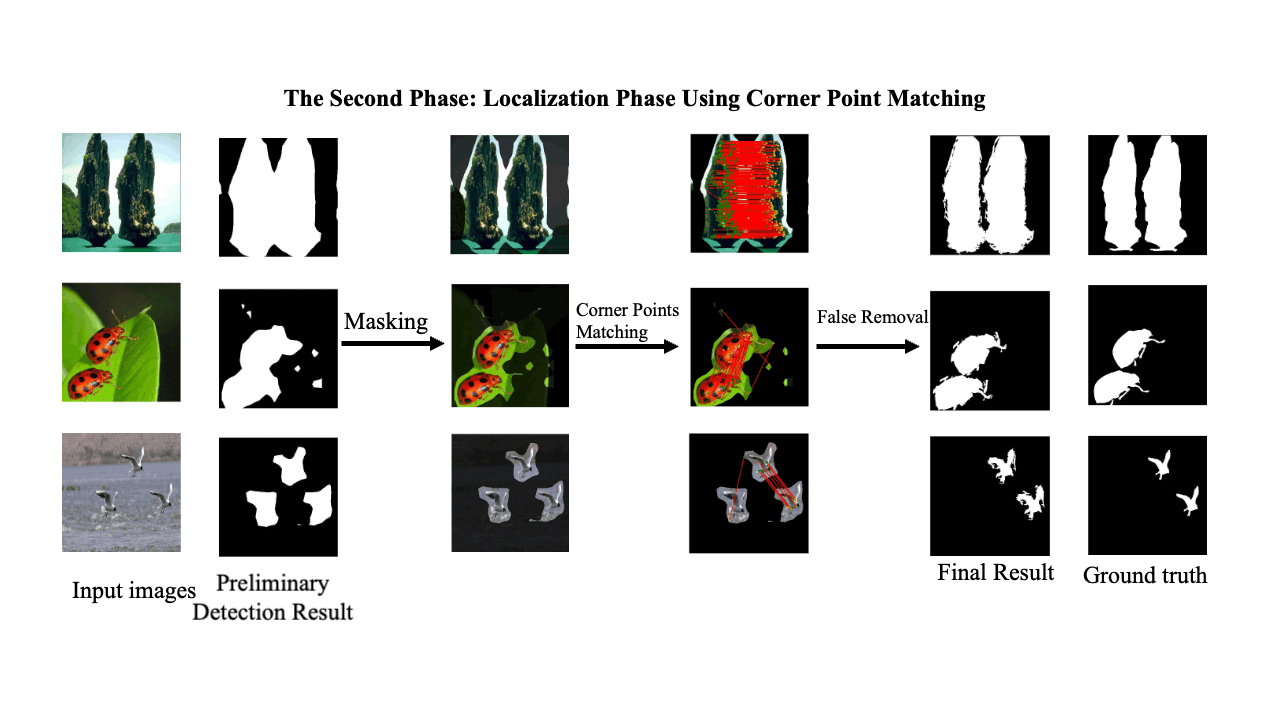
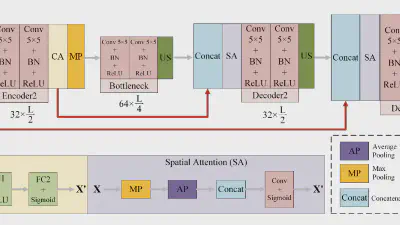
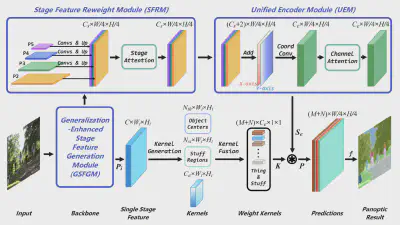
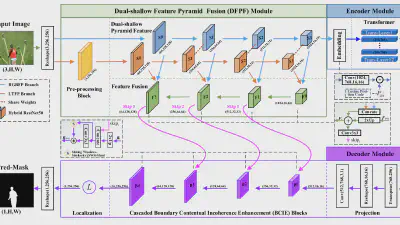
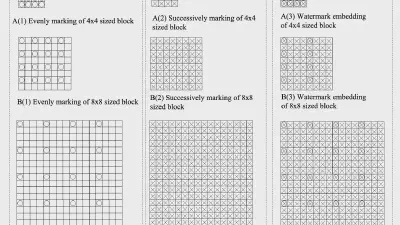
A Two-Phase Scheme by Integration of Deep and Corner Feature for Balanced Copy-Move Forgery Localization
In the era of Industry 4.0, the widespread application of digitization, automation, and Internet technology in industrial production has led to a significant increase in image …